It is important to note that HIPAA compliance in healthcare cybersecurity was an issue that was unknown 20 years ago. Technology has also progressed very quickly, which has introduced many benefits, however, it also poses a major challenge: maintaining the privacy of patient information.
At the heart of these privacy concerns is the Health Insurance Portability and Accountability Act (HIPAA), which was passed nearly 30 years ago. This is a comprehensive law designed to protect the privacy and security of health data.
A lot has changed since then, and with healthcare cyber security forecast to become a $25 billion industry by 2025, it’s clear that addressing breaches is a priority. However, navigating HIPAA compliance in healthcare cybersecurity in a rapidly evolving technology environment can be challenging.
How can cyber security professionals strike the right balance between technology and compliance while protecting patient privacy and data security?
Cyber security professionals play an important role in the healthcare field
As healthcare organizations increasingly rely on digital platforms, cyber professionals will become critical partners in ensuring the privacy, integrity and availability of sensitive healthcare data. But unlike traditional fields, healthcare presents unique challenges for online professionals.
The large and interconnected nature of health systems and the diversity of stakeholders present many potential vulnerabilities. From protecting medical devices to protecting electronic health records shared across networks, cyber professionals need to stay ahead of threats.
But when vulnerabilities are discovered to strengthen defenses, ethics must also respect the privacy and sanctity of medical data. It requires a level of style not seen in other fields.
Cyber Threats to Health Data
Cyber security threats protecting the healthcare sector include:
-
Ransom ware attacks:
These attacks can disrupt entire healthcare networks, compromise patient records and disrupt critical healthcare services. A good example is the infamous Wannacry attack that threw the UK healthcare system into chaos. This trend will continue, and many pharmacies in the United States will be targeted again.
-
Phishing attempts:
Healthcare workers and employees are often bombarded with emails and messages, putting them at high risk for phishing attacks. This risk is especially evident when trying to comply with HIPAA regulations when working with remote computers. This is because it is easy for an attacker to hack someone from another site or branch.
-
Insider Threats:
Insider threats involve people within an organization, such as employees and contractors, abusing their access and rights to compromise the privacy, integrity, or availability of or confidential information, including protected health information (PHI). Insider threats can result from unauthorized access to patient data, data theft, negligence, improper disclosure of PHI, or compromising system integrity.
HIPAA Compliance Guide for Cyber Professionals
We may implement various technologies and practices to protect the privacy, integrity and availability of your sensitive health information.
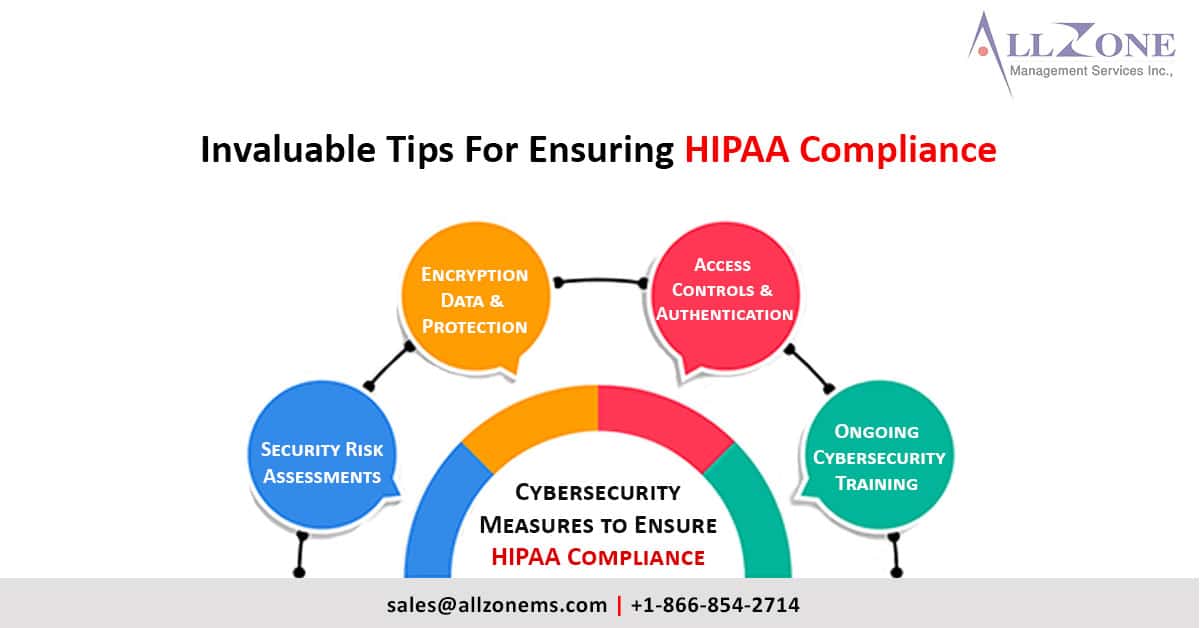
1. Security risk assessment
Security Risk Assessment The first important step in a security risk assessment is to carefully examine the healthcare infrastructure itself to identify potential vulnerabilities.
This includes carefully examining network configurations, software applications, and access controls to identify system weaknesses caused by outdated software, incorrect configurations, and inappropriate access restrictions.
When evaluating potential vulnerabilities, it is important to note that HIPAA does not address patient data, ongoing data management systems, or signing BAAs with third-party providers.
Instead, fulfillment should occur in site-specific workflows. Even seemingly innocuous software, such as text editors, messaging apps, and photo viewers, should be checked for HIPAA Compliance in Healthcare Cybersecurity before use.
2. Encryption and data protection strategies
Encryption is important, but there are many ways healthcare providers can protect data in transit and in databases. Installing strong encryption switches, regularly updating encryption keys, and implementing end-to-end encryption for communication channels are just some of the data protection measures that should be on your list.
In addition to this, you should also install a document lifecycle management system and a real-time monitoring and alerting system to alert you when data and flags change. Finally, like cybersecurity in general, encryption and data protection is not a “set it and forget it” issue.
Whether it’s identifying blind spots or just finding out where you need to improve, it’s very important to check the Internet regularly.
3. Authentication and access control
Unauthorized access to data is one of the biggest challenges to protecting medical data. Implementing secure access controls and authentication methods is one of the most effective lines of defense against these problems.
One way to control access is to implement an access control system that limits access to the system to people who have the necessary rights to view or modify certain types of patient data.
Another way to prevent unauthorized access is to use multifactor authentication (MFA). Add a layer of security by asking users to verify their identity in various ways, such as a password or a unique code generated by the authentication application. This reduces the risk of unauthorized access even if your login credentials are compromised.
4. Security Training
Organizations should conduct regular online training to recognize the warning signs of identity theft and equip employees with the skills to identify suspicious emails, links and messages that could compromise information security.
By creating a culture of vigilance and providing an understanding of the tactics used by cyberattacks, healthcare organizations can empower their employees to be a strong line of defense against cyberattacks. .
This includes everyone. Security professionals are often “on” or on the front lines, but there are still some who can play an important role in the home.
5. Response and Reports
Sometimes, despite the best efforts, accidents cannot be avoided. Healthcare organizations should have an incident response plan to manage these situations and minimize their impact.
The cornerstone of an effective incident response plan is the rapid detection and containment of security incidents.
Cyber professionals must set up monitoring systems to quickly identify malicious activity and breaches.
Expediting a health data breach requires not only a rapid response to the incident, but also compliance with HIPAA’s strict notification requirements, which require healthcare organizations to notify individuals as soon as possible.